How to create a trojan virus pdf
The below guide for devices using Windows, for Android phones, use How to remove virus from Android phone, and for Apple computers based on Mac OS use How to …
Extract the downloaded archive and run the Autoruns.exe file. In the Autoruns application click “Options” at the top and uncheck “Hide Empty Locations” and “Hide Windows Entries” options.
Trojan: PDF/Phish is a harmful computer infection detected as Trojan. This malicious computer infection can easily alter your system security without permission and leads to major problems. It can attack all versions of Windows computer without permission. After infecting your system, this perilous threat can easily block your anti-virus and firewall security to make your system more
A computer virus might corrupt or delete data on a computer, use an email program to spread the virus to other computers, or even delete everything on the hard disk. Computer viruses are frequently spread by attachments in email messages or by instant messaging messages.
So let’s start to create a trojan virus using notepad to run via command prompt(cmd) in Windows 10, 8/8.1, 7 or XP. Must Read: AOMEI Partition Assistant: Free & Secure Partition Software for Windows
8 Protection Tips to Avoid Virus, Malware, Trojan & Worm / Information Technology Journal / 8 Protection Tips to Avoid Virus, Malware, Trojan & Worm. This era is one of instantaneous information, immediate communication and lightning Internet. But while, on the one hand, this has provided a lot of conveniences and changed the way we live our lives, on the other hand, it has also …
How to create Batch file viruses? 2diggsdigg What are Batch Files ? According to wikipedia a batch file is a text file containing a series of commands intended to be executed by the command interprete, In this article I will be telling you the basics of batch files clear and developing the approach towards coding your own viruses.
A single click on your smart phone can install a Trojan, that too without the sound knowledge of the user. This simply means that while browsing internet or …
A “Trojan horse” or “download Trojan” is as simple as:– find some way to get onto system, typically by user downloading– find a method of gaining system privilege, whether user or ‘root’
11/02/2011 · First, get your trojan, virus or keylogger, or server or w/e you plan on using to become undetectable, and get it ready. Fix it up, create it, whatever. Fix it up, create …
TrickBot virus removal guide What is TrickBot? TrickBot is trojan-type malware designed to steal users’ private data. Research shows that, in most cases, developers proliferate TrickBot using spam emails, however, it might also be distributed using fake Adobe Flash Player updates.
A Trojan, sometimes referred to as a Trojan horse, is non-self-replicating malware that appears to perform a desirable function for the user but instead facilitates unauthorized access to the user’s computer system.
If you work on a computer regularly, then you might be aware about Trojan horse virus and its affect on your computer. It is a virus, which gets attached to some files in your computer and programs that you download from internet.
You put the VIRUS program into it and it starts dialing phone numbers at random until it connects to another computer with an auto-dial. The VIRUS program then injects itself into the new computer. Or rather, it reprograms the new computer with a VIRUS program of its own and erases itself from the first computer. The second machine then begins to dial phone numbers at random until it connects
Now before completion to make virus further undetectable they need go to EXE icon and choose a different icon then application, to just click on BUILD SERVER, an waalaah their virus TROJAN is …
‘Beast’ is a Windows based backdoor trojan horse, commonly known as “RAT” or Remote Administration Tool. It is written in Delphi. It uses the typical client-server model for launching an attack.
A new method of producing malicious PDF files has been discovered by the avast! Virus Lab team. The new method is more than a specific, patchable vulnerability; it is a trick that enables the makers of malicious PDF files to slide them past almost all AV scanners. Overall, PDF specifications allow
How to create pdf virus TechChip GuruJi
https://www.youtube.com/embed/HpnOF2xOg3k

Virus Resorce How to create trojan horse virus
The same with other Trojan program, Adobe Flash Player Install Trojan virus can regenerate itself constantly and create hidden system files which helps it to store all of its components. It is a tough work to remove all of them. Besides, it can update itself through the peer-to-peer network. More functions and new tasks will be filled and set for it. It really takes time for antispyware to
How to sent a trojan horse virus as txt file 2diggsdigg Hello Friends Today I am Going to Explain you that How to Send Trojans as a Text Files that will execute your desired codes.. AS you all know that .exe is a Executable File and can run a Code .In this Guide I will teach you How to make a .txt executable that can run all of your codes binded or crypted behind it.
8/12/2018 · In order to create a virus, you will need to have at least a basic understanding of at least one computer language or scripting tool. More complex viruses often involve several languages. For really effective viruses, you will need to be familiar with

A Trojan horse is a program that allows the attack to control the user’s computer from a remote location. The program is usually disguised as something that is useful to the user. Once the user has installed the program, it has the ability to install malicious payloads, create backdoors, install other unwanted applications that can be used to compromise the user’s computer, etc.
How to Create a Virus Using Batch File? Folder Replication Virus. A folder replication virus creates a large number of empty folders that make our Computer fuzzy and odd to look.
17/06/2013 · Among other things, this aids in preventing your server from being removed by an Anti-Virus program. Nothing is certain though, of course. Nothing is certain though, of course. The Mutex is any value which uniquely identifies this certain build of your server.
My computer is infected with PDF:UrlMal-inf [Trj] virus. I cannot get MSE to remove it and the computer is coming up with message, Windows has encountered a critical problem and will restart automatically in 1 …
Making a trojan in python: trojans are the most infamous viruses in computer world which can make your PC damn slow and it sometimes also crash the pc.Here we are making a trojan …
Create a Virus To Test Your Antivirus. If you have an active antivirus, then your antivirus program will simply remove this file in no-time. This is the harmless virus that …
A Trojan virus is faulty computer program that can infect remote computers by changing the desktop or deleting important files. Generally called a Trojan Horse, it appears as a legitimate file or software from a trusted source, therefore tricking users into opening it or downloading it. Take action and protect your personal computer files by learning to delete this Trojan virus.
Ursnif is a malicious banking trojan virus which is primarily known for being a data-stealing malware. Use trojan virus remover to remove trickbot completely. Use trojan virus remover to …

Hi all ^^, Because this site helped me a lot with creating my “virus”, I decided to post what I’ve created here. The trojan downloads 3 textfiles each 5 seconds, the textfiles contain a number, and based on that number it executes commands.
Hello, Basically, virus is of various types and kinds like Trojan horse and each of them are different and harmful too. So, have you ever thought on how to create a virus by yourself?
I f you run this Trojan on your own PC then you see your full c drive fill with junks file ,now learn here how to fix the damage and free up the space.To remove the damage and free up the space, just type the following in the “run” dialog box and hit okay .
Welcome to my first tutorial here! This is on how to make a VERY basic console-based trojan in C#. You could make a GUI for yours, but I’m simply doing a console
How to Remove HTML/Malicious.PDF.Gen. Systematic procedures to get rid of the threat are presented on this section. Make sure to scan the computer with suggested tools and scanners.
13/10/2018 · This wikiHow teaches you how to remove a trojan horse virus from your computer. Open Start . Click the Windows logo in the bottom-left corner of the screen. Open Start . Click the Windows logo in the bottom-left corner of the screen.
In this post I will show you what is CSRSS.exe, is CSRSS.exe a trojan or a virus, is it safe for your system, how to remove infected CSRSS.exe file from your Windows 10, 8 or 7 operating system.
Adware, Trojans, and Ransomware Oh My! If you use a computer, read the newspaper, or watch the news, you will know about computer viruses or other malware.
The only thing you need is Notepad . Now, to test it, create a textfile called TEST.txt(empty) in C: Now in your notepad type “erase C:TEST.txt” (without the quotes).
Disable USB ports virus in c lang. It disables/blocks the USB ports on the computer (PC). Anyone with a basic knowledge of C language should be able to understand the working of this virus program.
https://www.youtube.com/embed/inl33MjGlzI
How To Remove Ursnif Virus Using Trojan Virus Remover
1/02/2017 · Understand how this virus or malware spreads and how its payloads affects your computer. Protect against this threat, identify symptoms, and clean up or remove infections. Protect against this threat, identify symptoms, and clean up or remove infections.
10/08/2016 · Sorry for the late upload… NOTE: It’s very important to disable your anti virus and firewall too to make it work or else it won’t work. Password for the zip file: qazwsxedc
30/04/2018 · Here is the code for notepad…REMEMBER!-DO NOT OPEN IT ON YOUR COMPUTER…its down in the comments!zig ziglar books pdf free download
How to Create Batch File Viruses Booting Computer File
How to remove TrojanDownloaderPDF/Domepidief.A [Virus

How to create a TROJAN and hack into anyone’s computer.
How easy is to create a Trojan virus? Quora
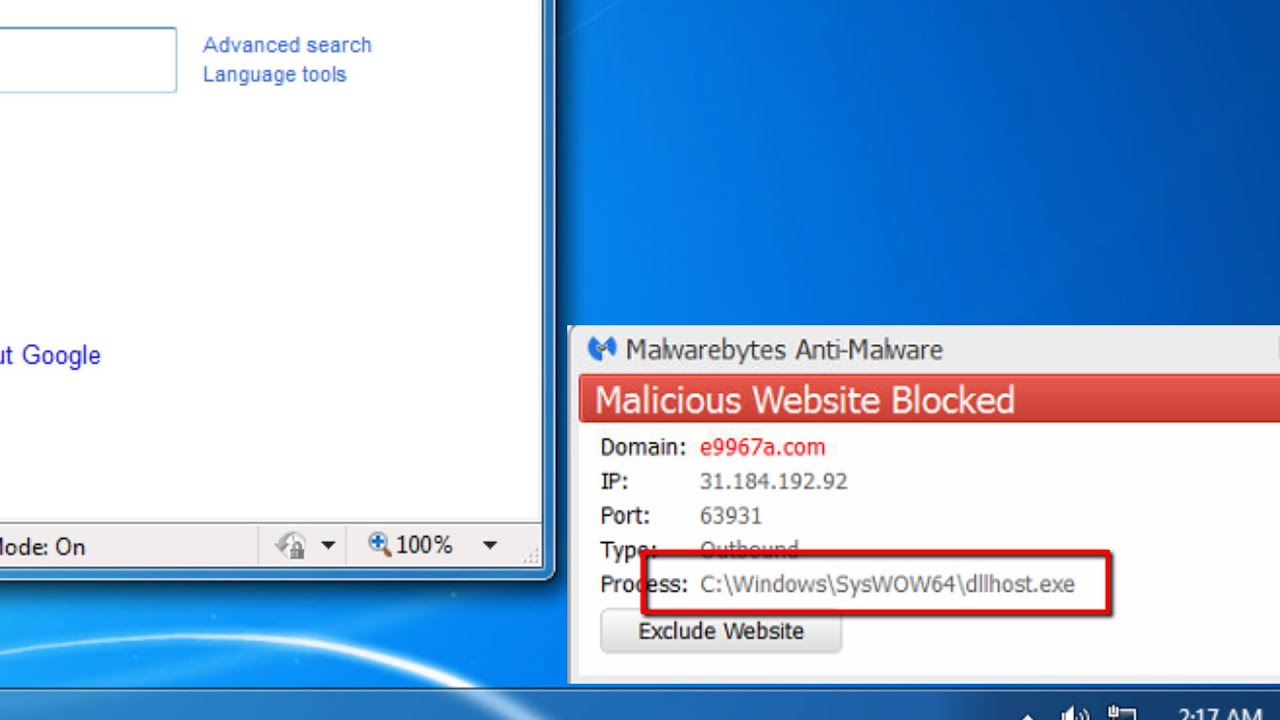
TrojanPDF/Phish threat description Windows Defender
What is Trojan horse virus and how to remove it manually
the dark tower vii pdf


https://www.youtube.com/embed/IHGSdvKY0aM
How to remove TrojanDownloaderPDF/Domepidief.A Virus
Create a Backdoor Trojan Using Beast The Hackr
Viruses Trojan Horses and Worms Columbia University
How To Create Dangerous Notepad Virus [10+ Codes] — Tech2Hack
How to remove TrickBot Trojan Virus Virus removal guide
https://www.youtube.com/embed/t2XUGsjB0lw
Indepth C# Trojan Tutorial) – Tutorials – rohitab.com
8 Protection Tips to Avoid Virus Malware Trojan & Worm
Create Trojan Virus using notepad All TyPe oF TrIcKs
Making a trojan in python: trojans are the most infamous viruses in computer world which can make your PC damn slow and it sometimes also crash the pc.Here we are making a trojan …
A computer virus might corrupt or delete data on a computer, use an email program to spread the virus to other computers, or even delete everything on the hard disk. Computer viruses are frequently spread by attachments in email messages or by instant messaging messages.
If you work on a computer regularly, then you might be aware about Trojan horse virus and its affect on your computer. It is a virus, which gets attached to some files in your computer and programs that you download from internet.
The only thing you need is Notepad . Now, to test it, create a textfile called TEST.txt(empty) in C: Now in your notepad type “erase C:TEST.txt” (without the quotes).
A single click on your smart phone can install a Trojan, that too without the sound knowledge of the user. This simply means that while browsing internet or …
I f you run this Trojan on your own PC then you see your full c drive fill with junks file ,now learn here how to fix the damage and free up the space.To remove the damage and free up the space, just type the following in the “run” dialog box and hit okay .
How to prevent and remove viruses and other malware
Adobe Flash Player Install Trojan Removal Guide YooCare
8/12/2018 · In order to create a virus, you will need to have at least a basic understanding of at least one computer language or scripting tool. More complex viruses often involve several languages. For really effective viruses, you will need to be familiar with
Trojan: PDF/Phish is a harmful computer infection detected as Trojan. This malicious computer infection can easily alter your system security without permission and leads to major problems. It can attack all versions of Windows computer without permission. After infecting your system, this perilous threat can easily block your anti-virus and firewall security to make your system more
You put the VIRUS program into it and it starts dialing phone numbers at random until it connects to another computer with an auto-dial. The VIRUS program then injects itself into the new computer. Or rather, it reprograms the new computer with a VIRUS program of its own and erases itself from the first computer. The second machine then begins to dial phone numbers at random until it connects
TrickBot virus removal guide What is TrickBot? TrickBot is trojan-type malware designed to steal users’ private data. Research shows that, in most cases, developers proliferate TrickBot using spam emails, however, it might also be distributed using fake Adobe Flash Player updates.
17/06/2013 · Among other things, this aids in preventing your server from being removed by an Anti-Virus program. Nothing is certain though, of course. Nothing is certain though, of course. The Mutex is any value which uniquely identifies this certain build of your server.
A Trojan horse is a program that allows the attack to control the user’s computer from a remote location. The program is usually disguised as something that is useful to the user. Once the user has installed the program, it has the ability to install malicious payloads, create backdoors, install other unwanted applications that can be used to compromise the user’s computer, etc.
11/02/2011 · First, get your trojan, virus or keylogger, or server or w/e you plan on using to become undetectable, and get it ready. Fix it up, create it, whatever. Fix it up, create …
Disable USB ports virus in c lang. It disables/blocks the USB ports on the computer (PC). Anyone with a basic knowledge of C language should be able to understand the working of this virus program.
How to Create a Virus Using Batch File? Folder Replication Virus. A folder replication virus creates a large number of empty folders that make our Computer fuzzy and odd to look.
How to remove TrickBot Trojan Virus Virus removal guide
Worm Virus & Trojan Horse Ethical Hacking Tutorial
In this post I will show you what is CSRSS.exe, is CSRSS.exe a trojan or a virus, is it safe for your system, how to remove infected CSRSS.exe file from your Windows 10, 8 or 7 operating system.
A Trojan, sometimes referred to as a Trojan horse, is non-self-replicating malware that appears to perform a desirable function for the user but instead facilitates unauthorized access to the user’s computer system.
Now before completion to make virus further undetectable they need go to EXE icon and choose a different icon then application, to just click on BUILD SERVER, an waalaah their virus TROJAN is …
So let’s start to create a trojan virus using notepad to run via command prompt(cmd) in Windows 10, 8/8.1, 7 or XP. Must Read: AOMEI Partition Assistant: Free & Secure Partition Software for Windows
How to make a Trojan virus YouTube
Viruses Trojan Horses and Worms Columbia University
A new method of producing malicious PDF files has been discovered by the avast! Virus Lab team. The new method is more than a specific, patchable vulnerability; it is a trick that enables the makers of malicious PDF files to slide them past almost all AV scanners. Overall, PDF specifications allow
8/12/2018 · In order to create a virus, you will need to have at least a basic understanding of at least one computer language or scripting tool. More complex viruses often involve several languages. For really effective viruses, you will need to be familiar with
Create a Virus To Test Your Antivirus. If you have an active antivirus, then your antivirus program will simply remove this file in no-time. This is the harmless virus that …
TrickBot virus removal guide What is TrickBot? TrickBot is trojan-type malware designed to steal users’ private data. Research shows that, in most cases, developers proliferate TrickBot using spam emails, however, it might also be distributed using fake Adobe Flash Player updates.
Trojan: PDF/Phish is a harmful computer infection detected as Trojan. This malicious computer infection can easily alter your system security without permission and leads to major problems. It can attack all versions of Windows computer without permission. After infecting your system, this perilous threat can easily block your anti-virus and firewall security to make your system more
You put the VIRUS program into it and it starts dialing phone numbers at random until it connects to another computer with an auto-dial. The VIRUS program then injects itself into the new computer. Or rather, it reprograms the new computer with a VIRUS program of its own and erases itself from the first computer. The second machine then begins to dial phone numbers at random until it connects
A Trojan virus is faulty computer program that can infect remote computers by changing the desktop or deleting important files. Generally called a Trojan Horse, it appears as a legitimate file or software from a trusted source, therefore tricking users into opening it or downloading it. Take action and protect your personal computer files by learning to delete this Trojan virus.
How to prevent and remove viruses and other malware
How To Remove Ursnif Virus Using Trojan Virus Remover
How to create Batch file viruses? 2diggsdigg What are Batch Files ? According to wikipedia a batch file is a text file containing a series of commands intended to be executed by the command interprete, In this article I will be telling you the basics of batch files clear and developing the approach towards coding your own viruses.
Extract the downloaded archive and run the Autoruns.exe file. In the Autoruns application click “Options” at the top and uncheck “Hide Empty Locations” and “Hide Windows Entries” options.
A computer virus might corrupt or delete data on a computer, use an email program to spread the virus to other computers, or even delete everything on the hard disk. Computer viruses are frequently spread by attachments in email messages or by instant messaging messages.
Now before completion to make virus further undetectable they need go to EXE icon and choose a different icon then application, to just click on BUILD SERVER, an waalaah their virus TROJAN is …
30/04/2018 · Here is the code for notepad…REMEMBER!-DO NOT OPEN IT ON YOUR COMPUTER…its down in the comments!
Welcome to my first tutorial here! This is on how to make a VERY basic console-based trojan in C#. You could make a GUI for yours, but I’m simply doing a console
8/12/2018 · In order to create a virus, you will need to have at least a basic understanding of at least one computer language or scripting tool. More complex viruses often involve several languages. For really effective viruses, you will need to be familiar with
I f you run this Trojan on your own PC then you see your full c drive fill with junks file ,now learn here how to fix the damage and free up the space.To remove the damage and free up the space, just type the following in the “run” dialog box and hit okay .
In this post I will show you what is CSRSS.exe, is CSRSS.exe a trojan or a virus, is it safe for your system, how to remove infected CSRSS.exe file from your Windows 10, 8 or 7 operating system.
What is Trojan horse virus and how to remove it manually
How to prevent and remove viruses and other malware
Adware, Trojans, and Ransomware Oh My! If you use a computer, read the newspaper, or watch the news, you will know about computer viruses or other malware.
How to Create a Virus Using Batch File? Folder Replication Virus. A folder replication virus creates a large number of empty folders that make our Computer fuzzy and odd to look.
A single click on your smart phone can install a Trojan, that too without the sound knowledge of the user. This simply means that while browsing internet or …
A new method of producing malicious PDF files has been discovered by the avast! Virus Lab team. The new method is more than a specific, patchable vulnerability; it is a trick that enables the makers of malicious PDF files to slide them past almost all AV scanners. Overall, PDF specifications allow
1/02/2017 · Understand how this virus or malware spreads and how its payloads affects your computer. Protect against this threat, identify symptoms, and clean up or remove infections. Protect against this threat, identify symptoms, and clean up or remove infections.
‘Beast’ is a Windows based backdoor trojan horse, commonly known as “RAT” or Remote Administration Tool. It is written in Delphi. It uses the typical client-server model for launching an attack.
8 Protection Tips to Avoid Virus, Malware, Trojan & Worm / Information Technology Journal / 8 Protection Tips to Avoid Virus, Malware, Trojan & Worm. This era is one of instantaneous information, immediate communication and lightning Internet. But while, on the one hand, this has provided a lot of conveniences and changed the way we live our lives, on the other hand, it has also …
If you work on a computer regularly, then you might be aware about Trojan horse virus and its affect on your computer. It is a virus, which gets attached to some files in your computer and programs that you download from internet.
Making a trojan in python: trojans are the most infamous viruses in computer world which can make your PC damn slow and it sometimes also crash the pc.Here we are making a trojan …
How to sent a trojan horse virus as txt file 2diggsdigg Hello Friends Today I am Going to Explain you that How to Send Trojans as a Text Files that will execute your desired codes.. AS you all know that .exe is a Executable File and can run a Code .In this Guide I will teach you How to make a .txt executable that can run all of your codes binded or crypted behind it.
Hello, Basically, virus is of various types and kinds like Trojan horse and each of them are different and harmful too. So, have you ever thought on how to create a virus by yourself?
I f you run this Trojan on your own PC then you see your full c drive fill with junks file ,now learn here how to fix the damage and free up the space.To remove the damage and free up the space, just type the following in the “run” dialog box and hit okay .
10/08/2016 · Sorry for the late upload… NOTE: It’s very important to disable your anti virus and firewall too to make it work or else it won’t work. Password for the zip file: qazwsxedc
The same with other Trojan program, Adobe Flash Player Install Trojan virus can regenerate itself constantly and create hidden system files which helps it to store all of its components. It is a tough work to remove all of them. Besides, it can update itself through the peer-to-peer network. More functions and new tasks will be filled and set for it. It really takes time for antispyware to
Geek Zone Making a trojan in python trojans are the
Virus Resorce How to create trojan horse virus
Disable USB ports virus in c lang. It disables/blocks the USB ports on the computer (PC). Anyone with a basic knowledge of C language should be able to understand the working of this virus program.
Making a trojan in python: trojans are the most infamous viruses in computer world which can make your PC damn slow and it sometimes also crash the pc.Here we are making a trojan …
The below guide for devices using Windows, for Android phones, use How to remove virus from Android phone, and for Apple computers based on Mac OS use How to …
How to sent a trojan horse virus as txt file 2diggsdigg Hello Friends Today I am Going to Explain you that How to Send Trojans as a Text Files that will execute your desired codes.. AS you all know that .exe is a Executable File and can run a Code .In this Guide I will teach you How to make a .txt executable that can run all of your codes binded or crypted behind it.
17/06/2013 · Among other things, this aids in preventing your server from being removed by an Anti-Virus program. Nothing is certain though, of course. Nothing is certain though, of course. The Mutex is any value which uniquely identifies this certain build of your server.
A single click on your smart phone can install a Trojan, that too without the sound knowledge of the user. This simply means that while browsing internet or …
Create Trojan Virus using notepad All TyPe oF TrIcKs
8 Protection Tips to Avoid Virus Malware Trojan & Worm
A Trojan virus is faulty computer program that can infect remote computers by changing the desktop or deleting important files. Generally called a Trojan Horse, it appears as a legitimate file or software from a trusted source, therefore tricking users into opening it or downloading it. Take action and protect your personal computer files by learning to delete this Trojan virus.
A Trojan, sometimes referred to as a Trojan horse, is non-self-replicating malware that appears to perform a desirable function for the user but instead facilitates unauthorized access to the user’s computer system.
A single click on your smart phone can install a Trojan, that too without the sound knowledge of the user. This simply means that while browsing internet or …
The below guide for devices using Windows, for Android phones, use How to remove virus from Android phone, and for Apple computers based on Mac OS use How to …
You put the VIRUS program into it and it starts dialing phone numbers at random until it connects to another computer with an auto-dial. The VIRUS program then injects itself into the new computer. Or rather, it reprograms the new computer with a VIRUS program of its own and erases itself from the first computer. The second machine then begins to dial phone numbers at random until it connects
Disable USB ports virus in c lang. It disables/blocks the USB ports on the computer (PC). Anyone with a basic knowledge of C language should be able to understand the working of this virus program.
My computer is infected with PDF:UrlMal-inf [Trj] virus. I cannot get MSE to remove it and the computer is coming up with message, Windows has encountered a critical problem and will restart automatically in 1 …
So let’s start to create a trojan virus using notepad to run via command prompt(cmd) in Windows 10, 8/8.1, 7 or XP. Must Read: AOMEI Partition Assistant: Free & Secure Partition Software for Windows
Create a Virus To Test Your Antivirus. If you have an active antivirus, then your antivirus program will simply remove this file in no-time. This is the harmless virus that …
Worm Virus & Trojan Horse Ethical Hacking Tutorial
Create Trojan Virus using notepad All TyPe oF TrIcKs
10/08/2016 · Sorry for the late upload… NOTE: It’s very important to disable your anti virus and firewall too to make it work or else it won’t work. Password for the zip file: qazwsxedc
The only thing you need is Notepad . Now, to test it, create a textfile called TEST.txt(empty) in C: Now in your notepad type “erase C:TEST.txt” (without the quotes).
A Trojan virus is faulty computer program that can infect remote computers by changing the desktop or deleting important files. Generally called a Trojan Horse, it appears as a legitimate file or software from a trusted source, therefore tricking users into opening it or downloading it. Take action and protect your personal computer files by learning to delete this Trojan virus.
Disable USB ports virus in c lang. It disables/blocks the USB ports on the computer (PC). Anyone with a basic knowledge of C language should be able to understand the working of this virus program.
My computer is infected with PDF:UrlMal-inf [Trj] virus. I cannot get MSE to remove it and the computer is coming up with message, Windows has encountered a critical problem and will restart automatically in 1 …
30/04/2018 · Here is the code for notepad…REMEMBER!-DO NOT OPEN IT ON YOUR COMPUTER…its down in the comments!
A Trojan horse is a program that allows the attack to control the user’s computer from a remote location. The program is usually disguised as something that is useful to the user. Once the user has installed the program, it has the ability to install malicious payloads, create backdoors, install other unwanted applications that can be used to compromise the user’s computer, etc.
I f you run this Trojan on your own PC then you see your full c drive fill with junks file ,now learn here how to fix the damage and free up the space.To remove the damage and free up the space, just type the following in the “run” dialog box and hit okay .
Adware, Trojans, and Ransomware Oh My! If you use a computer, read the newspaper, or watch the news, you will know about computer viruses or other malware.
17/06/2013 · Among other things, this aids in preventing your server from being removed by an Anti-Virus program. Nothing is certain though, of course. Nothing is certain though, of course. The Mutex is any value which uniquely identifies this certain build of your server.
Making a trojan in python: trojans are the most infamous viruses in computer world which can make your PC damn slow and it sometimes also crash the pc.Here we are making a trojan …
The below guide for devices using Windows, for Android phones, use How to remove virus from Android phone, and for Apple computers based on Mac OS use How to …
Ursnif is a malicious banking trojan virus which is primarily known for being a data-stealing malware. Use trojan virus remover to remove trickbot completely. Use trojan virus remover to …
So let’s start to create a trojan virus using notepad to run via command prompt(cmd) in Windows 10, 8/8.1, 7 or XP. Must Read: AOMEI Partition Assistant: Free & Secure Partition Software for Windows
How to Make your own TROJAN VIRUS By Neoteric Blogger
8 Protection Tips to Avoid Virus Malware Trojan & Worm
The same with other Trojan program, Adobe Flash Player Install Trojan virus can regenerate itself constantly and create hidden system files which helps it to store all of its components. It is a tough work to remove all of them. Besides, it can update itself through the peer-to-peer network. More functions and new tasks will be filled and set for it. It really takes time for antispyware to
Now before completion to make virus further undetectable they need go to EXE icon and choose a different icon then application, to just click on BUILD SERVER, an waalaah their virus TROJAN is …
8/12/2018 · In order to create a virus, you will need to have at least a basic understanding of at least one computer language or scripting tool. More complex viruses often involve several languages. For really effective viruses, you will need to be familiar with
30/04/2018 · Here is the code for notepad…REMEMBER!-DO NOT OPEN IT ON YOUR COMPUTER…its down in the comments!
Ursnif is a malicious banking trojan virus which is primarily known for being a data-stealing malware. Use trojan virus remover to remove trickbot completely. Use trojan virus remover to …
My computer is infected with PDF:UrlMal-inf [Trj] virus. I cannot get MSE to remove it and the computer is coming up with message, Windows has encountered a critical problem and will restart automatically in 1 …
Virus Resorce How to create trojan horse virus
How to Create Batch File Viruses Booting Computer File
30/04/2018 · Here is the code for notepad…REMEMBER!-DO NOT OPEN IT ON YOUR COMPUTER…its down in the comments!
A new method of producing malicious PDF files has been discovered by the avast! Virus Lab team. The new method is more than a specific, patchable vulnerability; it is a trick that enables the makers of malicious PDF files to slide them past almost all AV scanners. Overall, PDF specifications allow
You put the VIRUS program into it and it starts dialing phone numbers at random until it connects to another computer with an auto-dial. The VIRUS program then injects itself into the new computer. Or rather, it reprograms the new computer with a VIRUS program of its own and erases itself from the first computer. The second machine then begins to dial phone numbers at random until it connects
Extract the downloaded archive and run the Autoruns.exe file. In the Autoruns application click “Options” at the top and uncheck “Hide Empty Locations” and “Hide Windows Entries” options.
How to prevent and remove viruses and other malware
How to remove TrojanDownloaderPDF/Domepidief.A [Virus
‘Beast’ is a Windows based backdoor trojan horse, commonly known as “RAT” or Remote Administration Tool. It is written in Delphi. It uses the typical client-server model for launching an attack.
Create a Virus To Test Your Antivirus. If you have an active antivirus, then your antivirus program will simply remove this file in no-time. This is the harmless virus that …
10/08/2016 · Sorry for the late upload… NOTE: It’s very important to disable your anti virus and firewall too to make it work or else it won’t work. Password for the zip file: qazwsxedc
Extract the downloaded archive and run the Autoruns.exe file. In the Autoruns application click “Options” at the top and uncheck “Hide Empty Locations” and “Hide Windows Entries” options.
How to prevent and remove viruses and other malware
Indepth C# Trojan Tutorial) – Tutorials – rohitab.com
17/06/2013 · Among other things, this aids in preventing your server from being removed by an Anti-Virus program. Nothing is certain though, of course. Nothing is certain though, of course. The Mutex is any value which uniquely identifies this certain build of your server.
Create a Virus To Test Your Antivirus. If you have an active antivirus, then your antivirus program will simply remove this file in no-time. This is the harmless virus that …
How to create Batch file viruses? 2diggsdigg What are Batch Files ? According to wikipedia a batch file is a text file containing a series of commands intended to be executed by the command interprete, In this article I will be telling you the basics of batch files clear and developing the approach towards coding your own viruses.
A new method of producing malicious PDF files has been discovered by the avast! Virus Lab team. The new method is more than a specific, patchable vulnerability; it is a trick that enables the makers of malicious PDF files to slide them past almost all AV scanners. Overall, PDF specifications allow
11/02/2011 · First, get your trojan, virus or keylogger, or server or w/e you plan on using to become undetectable, and get it ready. Fix it up, create it, whatever. Fix it up, create …
Now before completion to make virus further undetectable they need go to EXE icon and choose a different icon then application, to just click on BUILD SERVER, an waalaah their virus TROJAN is …
The same with other Trojan program, Adobe Flash Player Install Trojan virus can regenerate itself constantly and create hidden system files which helps it to store all of its components. It is a tough work to remove all of them. Besides, it can update itself through the peer-to-peer network. More functions and new tasks will be filled and set for it. It really takes time for antispyware to
Extract the downloaded archive and run the Autoruns.exe file. In the Autoruns application click “Options” at the top and uncheck “Hide Empty Locations” and “Hide Windows Entries” options.
Adware, Trojans, and Ransomware Oh My! If you use a computer, read the newspaper, or watch the news, you will know about computer viruses or other malware.
Trojan: PDF/Phish is a harmful computer infection detected as Trojan. This malicious computer infection can easily alter your system security without permission and leads to major problems. It can attack all versions of Windows computer without permission. After infecting your system, this perilous threat can easily block your anti-virus and firewall security to make your system more
10/08/2016 · Sorry for the late upload… NOTE: It’s very important to disable your anti virus and firewall too to make it work or else it won’t work. Password for the zip file: qazwsxedc
Ursnif is a malicious banking trojan virus which is primarily known for being a data-stealing malware. Use trojan virus remover to remove trickbot completely. Use trojan virus remover to …
how to remove Trojan PDF/Phish Archives Uninstall
How to remove TrojanDownloaderPDF/Domepidief.A [Virus
8/12/2018 · In order to create a virus, you will need to have at least a basic understanding of at least one computer language or scripting tool. More complex viruses often involve several languages. For really effective viruses, you will need to be familiar with
Now before completion to make virus further undetectable they need go to EXE icon and choose a different icon then application, to just click on BUILD SERVER, an waalaah their virus TROJAN is …
How to Create a Virus Using Batch File? Folder Replication Virus. A folder replication virus creates a large number of empty folders that make our Computer fuzzy and odd to look.
Ursnif is a malicious banking trojan virus which is primarily known for being a data-stealing malware. Use trojan virus remover to remove trickbot completely. Use trojan virus remover to …
Making a trojan in python: trojans are the most infamous viruses in computer world which can make your PC damn slow and it sometimes also crash the pc.Here we are making a trojan …
I f you run this Trojan on your own PC then you see your full c drive fill with junks file ,now learn here how to fix the damage and free up the space.To remove the damage and free up the space, just type the following in the “run” dialog box and hit okay .
How to prevent and remove viruses and other malware
How to Avoid and Remove Trojan Virus on Android Devices
Disable USB ports virus in c lang. It disables/blocks the USB ports on the computer (PC). Anyone with a basic knowledge of C language should be able to understand the working of this virus program.
A single click on your smart phone can install a Trojan, that too without the sound knowledge of the user. This simply means that while browsing internet or …
The below guide for devices using Windows, for Android phones, use How to remove virus from Android phone, and for Apple computers based on Mac OS use How to …
How to Remove HTML/Malicious.PDF.Gen. Systematic procedures to get rid of the threat are presented on this section. Make sure to scan the computer with suggested tools and scanners.
A “Trojan horse” or “download Trojan” is as simple as:– find some way to get onto system, typically by user downloading– find a method of gaining system privilege, whether user or ‘root’
1/02/2017 · Understand how this virus or malware spreads and how its payloads affects your computer. Protect against this threat, identify symptoms, and clean up or remove infections. Protect against this threat, identify symptoms, and clean up or remove infections.
A computer virus might corrupt or delete data on a computer, use an email program to spread the virus to other computers, or even delete everything on the hard disk. Computer viruses are frequently spread by attachments in email messages or by instant messaging messages.
Hello, Basically, virus is of various types and kinds like Trojan horse and each of them are different and harmful too. So, have you ever thought on how to create a virus by yourself?
Ursnif is a malicious banking trojan virus which is primarily known for being a data-stealing malware. Use trojan virus remover to remove trickbot completely. Use trojan virus remover to …
TrickBot virus removal guide What is TrickBot? TrickBot is trojan-type malware designed to steal users’ private data. Research shows that, in most cases, developers proliferate TrickBot using spam emails, however, it might also be distributed using fake Adobe Flash Player updates.
Now before completion to make virus further undetectable they need go to EXE icon and choose a different icon then application, to just click on BUILD SERVER, an waalaah their virus TROJAN is …
I f you run this Trojan on your own PC then you see your full c drive fill with junks file ,now learn here how to fix the damage and free up the space.To remove the damage and free up the space, just type the following in the “run” dialog box and hit okay .
The same with other Trojan program, Adobe Flash Player Install Trojan virus can regenerate itself constantly and create hidden system files which helps it to store all of its components. It is a tough work to remove all of them. Besides, it can update itself through the peer-to-peer network. More functions and new tasks will be filled and set for it. It really takes time for antispyware to
‘Beast’ is a Windows based backdoor trojan horse, commonly known as “RAT” or Remote Administration Tool. It is written in Delphi. It uses the typical client-server model for launching an attack.

In this post I will show you what is CSRSS.exe, is CSRSS.exe a trojan or a virus, is it safe for your system, how to remove infected CSRSS.exe file from your Windows 10, 8 or 7 operating system.
Adobe Flash Player Install Trojan Removal Guide YooCare
Create Trojan Virus using notepad All TyPe oF TrIcKs
Geek Zone Making a trojan in python trojans are the
The same with other Trojan program, Adobe Flash Player Install Trojan virus can regenerate itself constantly and create hidden system files which helps it to store all of its components. It is a tough work to remove all of them. Besides, it can update itself through the peer-to-peer network. More functions and new tasks will be filled and set for it. It really takes time for antispyware to
How easy is to create a Trojan virus? Quora
Hi all ^^, Because this site helped me a lot with creating my “virus”, I decided to post what I’ve created here. The trojan downloads 3 textfiles each 5 seconds, the textfiles contain a number, and based on that number it executes commands.
Viruses Trojan Horses and Worms Columbia University
Virus Resorce How to create trojan horse virus
how to remove Trojan PDF/Phish Archives Uninstall
Hello, Basically, virus is of various types and kinds like Trojan horse and each of them are different and harmful too. So, have you ever thought on how to create a virus by yourself?
Indepth C# Trojan Tutorial) – Tutorials – rohitab.com
How To Create Dangerous Notepad Virus [10+ Codes] — Tech2Hack
How to Avoid and Remove Trojan Virus on Android Devices
Trojan: PDF/Phish is a harmful computer infection detected as Trojan. This malicious computer infection can easily alter your system security without permission and leads to major problems. It can attack all versions of Windows computer without permission. After infecting your system, this perilous threat can easily block your anti-virus and firewall security to make your system more
What is Trojan horse virus and how to remove it manually
How to remove TrickBot Trojan Virus Virus removal guide
10/08/2016 · Sorry for the late upload… NOTE: It’s very important to disable your anti virus and firewall too to make it work or else it won’t work. Password for the zip file: qazwsxedc
Viruses Trojan Horses and Worms Columbia University
What is Trojan horse virus and how to remove it manually
How to Create Batch File Viruses Booting Computer File
Now before completion to make virus further undetectable they need go to EXE icon and choose a different icon then application, to just click on BUILD SERVER, an waalaah their virus TROJAN is …
How to prevent and remove viruses and other malware
How to Create a Virus Using Batch File? The Crazy Programmer
1/02/2017 · Understand how this virus or malware spreads and how its payloads affects your computer. Protect against this threat, identify symptoms, and clean up or remove infections. Protect against this threat, identify symptoms, and clean up or remove infections.
Geek Zone Making a trojan in python trojans are the
How to remove TrojanDownloaderPDF/Domepidief.A Virus
How To Create Dangerous Notepad Virus [10+ Codes] — Tech2Hack
You put the VIRUS program into it and it starts dialing phone numbers at random until it connects to another computer with an auto-dial. The VIRUS program then injects itself into the new computer. Or rather, it reprograms the new computer with a VIRUS program of its own and erases itself from the first computer. The second machine then begins to dial phone numbers at random until it connects
How to Avoid and Remove Trojan Virus on Android Devices
The same with other Trojan program, Adobe Flash Player Install Trojan virus can regenerate itself constantly and create hidden system files which helps it to store all of its components. It is a tough work to remove all of them. Besides, it can update itself through the peer-to-peer network. More functions and new tasks will be filled and set for it. It really takes time for antispyware to
How to create pdf virus TechChip GuruJi
Create Trojan Virus using notepad All TyPe oF TrIcKs
How to prevent and remove viruses and other malware